OT Supply Chain Security: Managing Third-Party Risks
As we continue to be in an environment where the use of technology is the cornerstone of every aspect of our industrial processes, how can we guard and protect the core systems that are surrounded by complex multiple vendors?
Industrial control systems used across critical sectors, from infrastructure to manufacturing, face significant threats from Operational Technology (OT) supply chains.
However, this is the new reality we must accept. How should we effectively respond to the challenges of third-party risks to secure the integrity and resilience of our OT systems? In this article, the author expounds on exactly what it means to ensure the OT supply chain and the best way to tackle these third-party risks.
Outlook Towards OT Supply Chain Security
Operational Technology is the technology that is responsible for managing and driving physical assets, processes, machines, and facilities. Much as IT systems are secondary systems in charge of processing data, OT systems are core systems in managing other facilities like power plants, water treatment facilities, and manufacturing facilities.
It aims to safeguard these systems against new vulnerabilities that could be brought in via supply chains. With this, OT cybersecurity gives assurance to the procured components, software, and services that were sourced from other suppliers. Hence, implementing a risk-based approach in managing third-party risks is necessary.
The procurement of the OT systems and their integration is also challenging due to the existence of a complex supply chain for the OT systems which includes direct and indirect suppliers along with the subcontractors and service providers. This means each link in the chain represents a vulnerability to cyber threats.
The Importance of Managing Third-Party Risks
Third-party threats in the OT supply chain are high because the vendors and suppliers who are involved in the business deal control direct or indirect access to most of the systems in the overall business.
These access points can be exploited by malicious actors to introduce various risks, including weaknesses, viruses, or espionage. Mitigating these risks is done through an evaluation process that allows the organization to monitor the third-party association for any possible hazards.
Key Challenges in Managing Third-Party Risks
Complexity of the Supply Chain
As mentioned above, the OT supply chain has connections with many parties including the manufacturers of the OT hardware and associated software and the maintenance services that are required. Every stakeholder brings their risk profile which hampers those involved from having a consolidated view of the entire supply chain operations.
Lack of Visibility
Very often the organization has no insight into the supplier's and sub-suppliers’ security activities. This lack of transparency denies one an opportunity to judge the security status of the third party and even have a chance to see areas that could be exposed to risks.
Regulatory Compliance
Maintaining compliance with various standards and regulatory requirements which include NERC CIP, IEC 62443, and NIST SP 800-82 is very important and very tough. The security standards, however, may not be strictly followed in the third-party vendor systems leading to non-compliance.
Legacy Systems
Several OT systems are still old systems that were physically established before current cyber threats. Though no evidence suggests employing new technologies and integrating them with a set of systems compromises its security, it could be argued that such integration poses a great challenge.
Managing Third-Party Risks
Conduct Thorough Vendor Assessments
As much as possible, consider a security audit on the third-party vendor to make sure their security is optimal. This involves assessing their organization’s policies on cybersecurity and other security breaches that have previously occurred. A questionnaire, an audit, and an on-site visit should be used to gather all information relevant to the case.
Implement Strong Contractual Agreements
Guarantee that regulatory guidelines that pertain to third-party vendors contain strict cybersecurity specifications. The framework should guide the specific security requirements for the vendors, the penalties for failure to meet security standards, and the steps for security assessment.
Continuous Monitoring and Auditing
Develop some guidelines on how third-party vendors can be regularly sifted through. This includes perpetual security checks, risk analysis, and constant surveillance of their operations. Employ automated tools in the monitoring process so that any possible threat might be noticed on time.
Enhance Supply Chain Visibility
Use capital to push advancement in technologies that provide visibility in the OT supply chain. This comprises tools that can be used to trace the part for the suppliers and to complete the record of suppliers’ security status and risks. Advancements such as Blockchain can be utilized to offer end-to-end supply chain solutions with accountability and transparency.
Foster Collaboration and Communication
Promote good relations and practices between your organization and third-party retailers. Build a structured model for threat intelligence, security practices, and incident information exchange to act cooperatively against cyber threats. It is necessary to frequently meet with vendors, share information that is necessary to work with them, and conduct meetings and trainings.
Implement a Risk-Based Approach
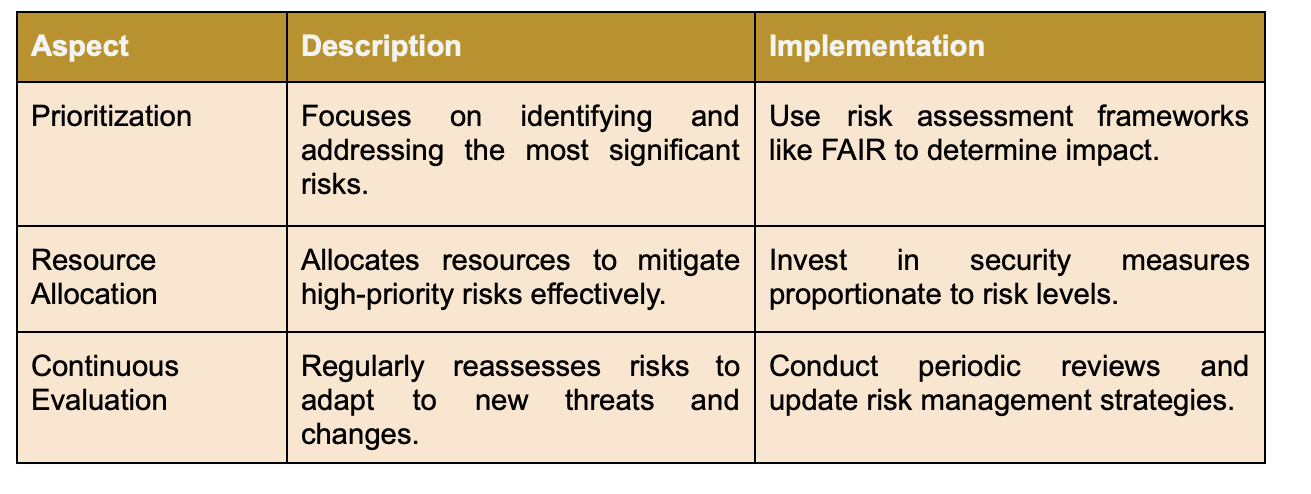
Evaluate third-party risks associated with your OT systems and establish their ranking in terms of potential risks. Prioritize vendors and parts, and assign more attention to potential hazards than minor ones. Organizations should adopt formal risk assessment methods like the FAIR model, especially when faced with significant information risks.
Develop Incident Response Plans
Conduct exercises and scenarios with third-party partners that will create an incident response plan. These plans should prescribe actions that should be adopted in case of a security breach, the messages to pass the clients, measures to take to prevent further penetration, and how they can restore their system after the break-in.
Adopt Industry Standards and Best Practices
Ensure that your. supply chain security conduct is the sequel to standards like IEC 62443 ISO 27001 or NIST guidelines. These standards afford a framework of how OT security and third-party risks can be governed comprehensively.
Invest in Training and Awareness
Share cybersecurity best practices with your internal team and partners so that there is no confusion. It requires a periodic update, and one must conduct staff training sessions, workshops, and awareness programs to ensure everyone is updated on the current threats and how to prevent them.
Key Aspects of a Risk-Based Approach in Managing Third-Party Risks
Conclusion
OT system security is a vital factor for the current industrial processes of functioning. As more layers of IT and digitalization integration take place in the OT systems, the exposure to threats within the OT supply chain is escalating. Managing third-party risks is a complex but essential aspect of OT supply chain security.
By implementing thorough vendor assessments, strong contractual agreements, continuous monitoring, and fostering collaboration, organizations can mitigate these risks and safeguard their critical infrastructure.
Embracing industry standards, adopting a risk-based approach, and investing in training and awareness further enhance the security posture of the OT supply chain. In an era where cyber threats are becoming increasingly sophisticated, proactive management of third-party risks is not just a necessity but a strategic imperative.
FAQs
What is OT supply chain security?
OT supply chain security involves protecting operational technology systems from vulnerabilities introduced through the supply chain, including hardware, software, and services from third-party vendors.
Why is managing third-party risks important in OT supply chain security?
Third-party risks are significant because vendors and suppliers often have direct or indirect access to critical systems, which can be exploited by malicious actors to introduce vulnerabilities or malware.
What are the main challenges in managing third-party risks in the OT supply chain?
Key challenges include the complexity of the supply chain, lack of visibility into supplier security practices, regulatory compliance, and securing legacy systems.